Backtrack has lots of tools for
web-application testing. Directory traversal is one of the critical
vulnerability in web-application. Previously i post about what is directory traversal & how to bypass its filter
, but that process is manual, it can consume lots of time.But in
bactrack automatic tools are available for this test which is DOTDOTPWN.
If you are on other distro , then you can download it form here.
It's a very flexible intelligent fuzzer to discover traversal directory vulnerabilities in software such as HTTP/FTP/TFTP servers, Web platforms such as CMSs, ERPs, Blogs, etc.
Also, it has a protocol-independent module to send the desired payload to the host and port specified. On the other hand, it also could be used in a scripting way using the STDOUT module.
It's written in perl programming language and can be run either under *NIX or Windows platforms. It's the first Mexican tool included in BackTrack Linux .
- HTTP
- HTTP URL
- FTP
- TFTP
- Payload (Protocol independent)
- STDOUT
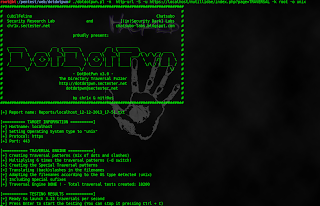
./dotdotpwn.pl -m http-url -S -u https://localhost/mutillidae/index.php?page=TRAVERSAL -k root -o unix
In below figure; you can see vulnerable URL where directory traversal is applicable.
If you are on other distro , then you can download it form here.
It's a very flexible intelligent fuzzer to discover traversal directory vulnerabilities in software such as HTTP/FTP/TFTP servers, Web platforms such as CMSs, ERPs, Blogs, etc.
Also, it has a protocol-independent module to send the desired payload to the host and port specified. On the other hand, it also could be used in a scripting way using the STDOUT module.
It's written in perl programming language and can be run either under *NIX or Windows platforms. It's the first Mexican tool included in BackTrack Linux .
Fuzzing modules supported in this version:
- HTTP
- HTTP URL
- FTP
- TFTP
- Payload (Protocol independent)
- STDOUT
./dotdotpwn.pl -m http-url -S -u https://localhost/mutillidae/index.php?page=TRAVERSAL -k root -o unix
In below figure; you can see vulnerable URL where directory traversal is applicable.

Post a Comment