 HOW TO: Make your computer talk like Iron man's Jarvis
HOW TO: Make your computer talk like Iron man's Jarvis
You Must have Watched The Movie "IRON MAN","The Avengers" and Tony Stark's Talkin...
Tutorials for hacking and basic concepts of hacking are taught here :) post your queries to us and tutorial will be posted by us ;)
 HOW TO: Make your computer talk like Iron man's Jarvis
HOW TO: Make your computer talk like Iron man's Jarvis
You Must have Watched The Movie "IRON MAN","The Avengers" and Tony Stark's Talkin...
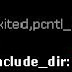 BYPASS DISABLED FUCTIONS AND 403 FORBIDDEN
BYPASS DISABLED FUCTIONS AND 403 FORBIDDEN
Hey guyz wazz up ? Em Here wid a new shit ! Very Use Full For Newbies As yewh know guys today most Of the server administrators Disable...
 BYPASS /etc/named.conf Symlink
BYPASS /etc/named.conf Symlink
Hey Noobies Watz up buddies haaan ? Em here wid a New Post. Well Guyz Now adays the Most God damn Problem Of linux servers is that admin ...
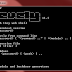 Weevely for Windows
Weevely for Windows
Weevely is a stealth PHP web shell that provides a telnet or netcat type console and let you execute command remotely. ...
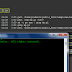 Back Connect Without Port Forward
Back Connect Without Port Forward
Hello guys Today I am Gonna give you a tutorial on back connecting As You know port forwarding is necessary for back connecting With a ...
 Rooting a server
Rooting a server
Rooting server Rooting a server Today I am going to give you a tutorial about rooting a server. Okay ...
 Unrestricted File Upload
Unrestricted File Upload
Description Uploaded files represent a significant risk to applications. The first step in many attacks is to get some code to the sy...
 Advanced Exploits Using XSS SHELL
Advanced Exploits Using XSS SHELL
Before understanding what XSS Shell is, let us recall a few basics of XSS (Cross Site Scripting). XSS is one of the most common vulnerabi...
 Testing for Reflected Cross site scripting
Testing for Reflected Cross site scripting
Brief Summary Reflected Cross-site Scripting (XSS) occur when an attacker injects browser executable code within a single HTTP respo...
 Web Application Exploits and Defenses
Web Application Exploits and Defenses
Client-State Manipulation When a user interacts with a web application, they do it indirectly through a browser. When the user clicks a b...