 YouTube Malvertising : Ads on YouTube leads users to Sweet Orange exploit kit
YouTube Malvertising : Ads on YouTube leads users to Sweet Orange exploit kit
YouTube Ads lead to exploit kits, YouTube serving ‘malvertising’? You may have heard of the term malvertising and threats posed by it. ...
Tutorials for hacking and basic concepts of hacking are taught here :) post your queries to us and tutorial will be posted by us ;)
 YouTube Malvertising : Ads on YouTube leads users to Sweet Orange exploit kit
YouTube Malvertising : Ads on YouTube leads users to Sweet Orange exploit kit
YouTube Ads lead to exploit kits, YouTube serving ‘malvertising’? You may have heard of the term malvertising and threats posed by it. ...
 Protect Your System from the Shellshock Exploit
Protect Your System from the Shellshock Exploit
On Wednesday, the world learned about a bug in the popular Unix, Linux, and Mac OS X command line interpreter Bash. Discovered by engin...
 Every Mac Is Vulnerable to the Shellshock Bash Exploit: Here's How to Patch OS X
Every Mac Is Vulnerable to the Shellshock Bash Exploit: Here's How to Patch OS X
Heartbleed, move over. There's a new bug in town, and this time it's also affecting Mac and Linux computers. It's called Shel...
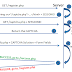 CAPTCHA Re-Riding Attack
CAPTCHA Re-Riding Attack
CAPTCHA Re-Riding Attack bypasses the CAPTCHA protection built into the web applications. The attack exploits the fact that the code that...
 How a Platform Using HTML5 Can Affect the Security of Your Website
How a Platform Using HTML5 Can Affect the Security of Your Website
How a Platform Using HTML5 Can Affect the Security of Your Website tl;dr Abstract To improve performa...
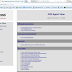 Cross Site Port Attacks - XSPA - Part 3
Cross Site Port Attacks - XSPA - Part 3
In the last 2 posts we saw what Cross Site Port Attacks (XSPA) are and what are the different attacks that are possible via XSPA. This po...
 Cross Site Port Attacks - XSPA - Part 2
Cross Site Port Attacks - XSPA - Part 2
This is the second post in the 3 part series that explains XSPA, the attacks and possible countermeasures. Read Cross Site Port Attacks - ...